When I started my IT career over 20 years ago, the threat landscape wasn’t quite threatening.
The world experienced a handful of viruses a year. They had pleasant names like “I LOVE YOU,” “HAPPY 99,” and even “ANNA KOURNIKOVA.” They were inviting.
Don’t get me wrong. These attacks weren’t benign; they did damage. Some even drove up costs estimated into the billions of dollars in lost time and productivity worldwide.
Back then, it seemed so distant. We knew what to do, had time to do it, and could get it done for those of us managing the risk – some antivirus here, some patches there, a firewall, a file backup system.
Today, when I am engaging leaders of organizations, both technical and non, I get the sense that they haven’t fully grasped the enemy’s current state.
Who are these people? How do they work? Why would they attack us? How would they attack us? What do they do? Why do they do it?
I don’t think these questions, or their answers, were all that important 20 years ago. Today I think they are critical, and not just for us in banking.
These critical questions are being overlooked in large part because we, like bankers, are focused on our controls, our cyber security framework, alignment, and readiness.
We are thinking about our ability to identify, protect, detect, respond and recover. We are doing this from the viewpoint of an administrator. What do the standards say? Do we have the right boxes checked? Are we compliant?
I am not critical of this approach. It is necessary and valuable. It drives less risk and greater readiness.
I am simply advocating that leaders get to know their enemy better before they find themselves facing off with them.
Five enemy attributes all banking leaders should understand:
1. The enemy has an attack framework. No different than we have a security framework.
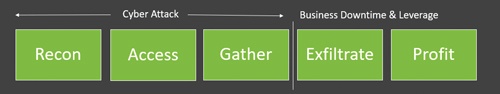
2. If you understand this framework, you’ll work better strategically to prepare and better tactically during an attack.
3. We aren’t dealing with a single attacker or even a group. The enemy is made up of many different organizations, businesses, and areas of specialty. They don’t all get paid the same way or at the same time. It is a professional outsourcing marketplace at a sophisticated, industrial scale. There is an entire industry around recon – finding organizations that fit specific criteria – and then selling that information – another industry that works to gain access using the recon information purchased. They sell that access to the next group, who are experts at gathering intelligence within the environment that could be leveraged for true profits in the right hands. This approach has made the enemy diverse in its skills, motives, tools, best practices, etc. It has also made their business very commercially viable while managing the risk of getting caught and apprehended. The majority of the perpetrators are in the research and development business, not conducting the actual dirty work and making it all the more palatable for their workforce.
4. Eventually, the enemy must create leverage and maximize profits. Leverage isn’t simply encrypting some essential files and then requesting a payment. The enemy has a playbook for turning up the heat. They are willing to be an anonymous whistleblower to the media, call customers directly to inform them of what’s going on, notify regulators before you may be prepared to address their questions, leak internal documents and emails, leverage your insurance coverages by reading your policy before they alert you to their presence, halt your technical operations through other forms of attack keeping you from conducting day to day business.
5. The enemy is using your tools against you. Why use a malicious tool that could be easily detected when you could use a safe tool already ready for malicious purposes? This change in tactics is making legacy detection methods less useful in the fight.
6. The enemy does not target you or your organization specifically. It isn’t personal. You are a transaction to the enemy, nothing more. Reconnaissance showed a technical vulnerability that was exploitable. That’s what created the target for the enemy. Nothing more. Montana organizations have a false sense of security because we think we are off the map. We are not!
Cybersecurity articles often create fear. Maybe that’s not a bad thing. However, it is not my intent. Too many leaders have defined this problem as too technical, complex and expensive, and possibly too scary. This definition leads to avoidance of the problem. This approach isn’t acceptable in banking, obviously.
Montana Independent Bankers need acceptance and action that is not only preventative but also helpful in the event of a response. Knowing thy enemy should help on both fronts of this escalating battle.
For more information on First Call Computer Solutions please visit firstsolution.com.








